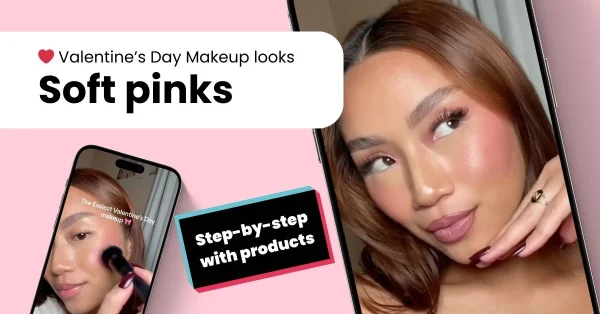
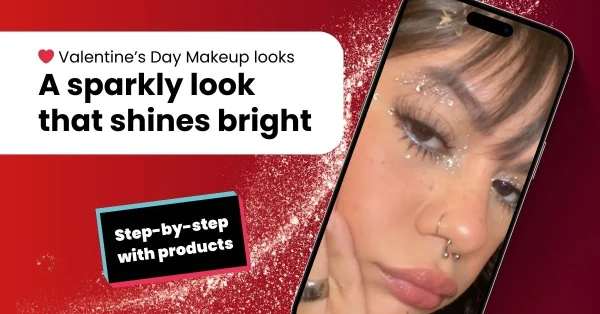
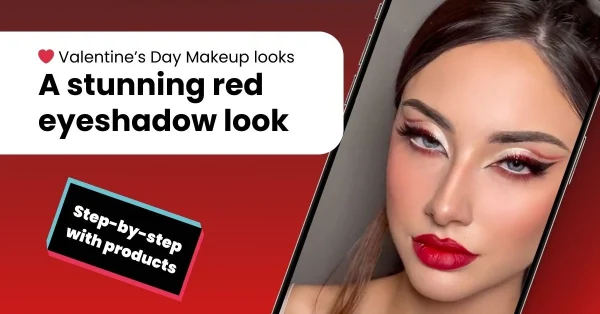
Latest articles
Lookfantastic review: How fantastic is it?
March 4, 2024
How to get Kiehl’s free samples
February 22, 2024
How to get your hands on coupons for free gifts from Kiehl’s in 2024
February 22, 2024
9 Makeup Trends You’ll Be Seeing Everywhere In 2024
February 26, 2024